ZK
Zybrea Knight
Answers (11)
ZK
Answered
________ is the actual speed of data transfer that is achieved between two nodes on a network and is always less than or equal to the data transfer rate.
A) Benchmark
B) Broadband
C) LAN speed
D) Throughput
A) Benchmark
B) Broadband
C) LAN speed
D) Throughput
On Jul 10, 2024
D
ZK
Answered
A(n) _____ allows you to run macro actions based on the result of a conditional expression.
A) If statement
B) query
C) Group program flow
D) Run statement
A) If statement
B) query
C) Group program flow
D) Run statement
On Jul 08, 2024
A
ZK
Answered
What is an ISP?
A) A telecommunications company that sells Internet access.
B) A communications device that connects to a communications channel.
C) A central point for cables in a network for data sharing,
D) A system of two or more devices linked by wires, cables, or a telecommunications system.
A) A telecommunications company that sells Internet access.
B) A communications device that connects to a communications channel.
C) A central point for cables in a network for data sharing,
D) A system of two or more devices linked by wires, cables, or a telecommunications system.
On Jun 08, 2024
A
ZK
Answered
What are the rules of total ordering?
On Jun 07, 2024
Total ordering says that the following rules must be satisfied:
1.Irreflexive)For no object o does o come before o.
2.Trichotomy)For any two objects o1 and o2,one and only one of the following holds true: o1 comes before o2,o1 comes after o2,or o1 equals o2.
3.Transitivity)If o1 comes before o2 and o2 comes before o3,then o1 comes before o3.
1.Irreflexive)For no object o does o come before o.
2.Trichotomy)For any two objects o1 and o2,one and only one of the following holds true: o1 comes before o2,o1 comes after o2,or o1 equals o2.
3.Transitivity)If o1 comes before o2 and o2 comes before o3,then o1 comes before o3.
ZK
Answered
Forward auctions typically result in ___ prices over time.
On Jun 05, 2024
higher
ZK
Answered
The move instruction copies data from a ____ word to a ____ word.
A) source, destination
B) destination, source
C) integer, floating point
D) floating point, integer
A) source, destination
B) destination, source
C) integer, floating point
D) floating point, integer
On May 09, 2024
A
ZK
Answered
Identity theft is a deliberate threat to information systems and is one of the largest concerns of consumers and businesses today. What are the four techniques the book mentions for illegally obtaining information? How can you protect yourself from each of these threats?
On May 08, 2024
1) Dumpster diving - shred your sensitive information 2) Stealing personal information in computer databases - have strong passwords, encrypt the data 3) Infiltrating organizations (data aggregators) that store large amounts of personal information - have strong passwords, encrypt the data 4) Phishing - never provide a user ID and password; always ensure the person/site is legitimate
ZK
Answered
When you insert a chart on a slide using the Charts button in a content placeholder or the Charts button on the Insert tab, which of the following opens so that you can enter the data for the chart?
A) An Excel worksheet
B) A legend
C) A hyperlink to an Excel worksheet
D) A PowerPoint table
A) An Excel worksheet
B) A legend
C) A hyperlink to an Excel worksheet
D) A PowerPoint table
On May 06, 2024
A
ZK
Answered
For the file copy (COP) instruction rung shown: 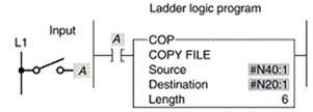
A) both source and destinations are file addresses.
B) when input A goes true, the values in file N40 are copied to N20.
C) both file N40 and N20 contain 6 words.
D) all of these

A) both source and destinations are file addresses.
B) when input A goes true, the values in file N40 are copied to N20.
C) both file N40 and N20 contain 6 words.
D) all of these
On May 05, 2024
D